If you want to secure connection to a resource on your apache web-server by using public key encryption technique then you can add the mod_ssl module into the apache web-server for that purpose.
Here are the list of things that are explained in this tutorial:-
I hope this was informational enough theory and now we can really proceed with the installation of mod_ssl on apache.
You can create a named host or a host based on ip address. In this we are going to setup the ip based virtual host.
Then we have to add the AddType directives so that apache recognizes the certificate files and their extensions. We will be adding the following two directives:
AddType application/x-x509-ca-cert .crt
AddType application/x-pkcs7-crl .crl
From the code box below just copy and paste the code into the httpd.conf.
But before that you would have to enable the mod_ssl module in the httpd.conf. To do that just open the httpd.conf and scroll down to the LoadModule directives and find one with the name mod_ssl and remove the # comment from before it as shown in the following figure.

From the code box below just copy and paste the code into the httpd.conf
You should add an exception for this after which the browser will download the CA certificate and you should see default apache web server page if successful. In mozilla certificate details can be seen by clicking on the navigation bar as shown below.

This is about it now we have set up and tested the SSL over http and hope this tutorial was helpful in making you understand the core concept behind digital certificates(X.509) public key encryption standard and setting up mod_ssl on your apache installation.
Here are the list of things that are explained in this tutorial:-
- Installing OpenSSL
- Public key encryption standard.
- Certificate Signing Authority(CA) and Digital Signatures
- Encryption Of Data (shared secret key encryption)
- Creating the Digital Certificate.
- Installing the certificate's and keys in proper directory
- Setting up the apache configuration(httpd.conf)
- Testing the configuration
1.Installing OpenSSL
The apache web server comes now bundled with and mod_ssl module.You can directly download the version 2.13 of apache web server from this link.
We need OpenSSL for producing digital certificates and what are these will be examined later on.
Just open and run the installer and after you have done that proceed to the second step and note that you may also need to download the OpenSSL module seperately for windows and also need to have the visual C++ modules for it to run. You can download these from this link.
The apache web server comes now bundled with and mod_ssl module.You can directly download the version 2.13 of apache web server from this link.
We need OpenSSL for producing digital certificates and what are these will be examined later on.
Just open and run the installer and after you have done that proceed to the second step and note that you may also need to download the OpenSSL module seperately for windows and also need to have the visual C++ modules for it to run. You can download these from this link.
2.Public key encryption standard: The public key encryption in short works as follows:-
There are essentially two pairs of keys per entity. One key which is shared and used to encrypt the contents and is publicly available is called public key whereas the other key which is used for decryption is called the private key is kept secret.
So if an entity 'A' has to send a secret message to entity 'B' then entity 'A' uses entity 'B's' public key to encrypt the message and on the receiving side entity 'B' uses its private key to decrypt the message and since only entity 'B' is in possession of it's private key therefore no third party can decrypt the content's of message.Unless Of-course the private key has been compromised.
The point that should be noted is that entity 'B' cannot guarantee that it is receiving message from entity 'A' because anyone with access to 'B's' public key can send B a message , therefore this communication lacks authentication.
There are essentially two pairs of keys per entity. One key which is shared and used to encrypt the contents and is publicly available is called public key whereas the other key which is used for decryption is called the private key is kept secret.
So if an entity 'A' has to send a secret message to entity 'B' then entity 'A' uses entity 'B's' public key to encrypt the message and on the receiving side entity 'B' uses its private key to decrypt the message and since only entity 'B' is in possession of it's private key therefore no third party can decrypt the content's of message.Unless Of-course the private key has been compromised.
The point that should be noted is that entity 'B' cannot guarantee that it is receiving message from entity 'A' because anyone with access to 'B's' public key can send B a message , therefore this communication lacks authentication.
3. Certificate Signing Authority(CA) and Digital Signatures:-
The only problem with the previous scheme was that the client cannot be sure that the sender is who he claims to be and this is where a CA comes in as it is responsible for verifying the details of the sender and issuing the X.509 digital certificate to it. The X.509 digital certificate contains the sender's public key,domain identifiers,serial number for the certificate and most importantly the encrypted hashed(md5 hash, RSA encryption) data (Encryption is done using CA's private key,The hashed data encrypted using CA'S key serves as Digital signature of the CA). This constitutes sender's certificate.
The sender (server), when sending information to the client may choose to encrypt the entire contents or just calculate an SHA-1 hash and encrypt it using it's private key and sends the X.509 digital certificate it obtained from the CA along with this.
On the client side firstly the the CA is identified by 'CA attribute' in the X509v3 extension section of x.509 digital certificate, then using CA's public key (stored in the browser in the CA certificate public key info) the hash is decrypted and this decrypted hash is compared with the hash that is calculated over the rest of the x.509 digital certificate that was sent by the sender. If these hash values match then client can be sure that this certificate really was signed by the CA and hence can be sure of the server that is sending the data because it was signed by the CA. The client then can decrypt the contents of the message by using the public key found in the x.509 digital certificate.
There are many well known certificate authorities such as Verisign etc whose certificates are not to be signed by any authority as they are the root certificate authorities and there certificates already come pre-installed in the browsers like Firefox, Internet Explorer etc. you can view them in mozilla firefox by going to Tools->Options->Advanced-> Encyption and then choosing View Certificates.
The only concern with getting the certificate signed by a CA is the cost factor.But on the other hand, This trusted third party scheme is more secure because in case the sender(server) loses its private key then it can ask the CA to revoke its certificate doing so places the certificate in CRL (Certificate Revocation List) which ensures that no one else can pretend to be the sender.
It may happen that once in a while you may encounter that if you are viewing a site in mozilla you may encounter that mozilla displays you a warning message as shown below which warns you that you may be at risk viewing the website, this happens only due to the fact that the certificate may be self-signed by the server or a CA not known to the browser and therefore the authenticity of the sender cannot be known and hence you should avoid sending personal details over to a web server like that because if the private key of the server is compromised then it can lead to potential fraudulent activity. However, if you do trust the server you can click on proceed and this leads to saving of the CA certificate of the server's CA on your browser and then you can view the certificate as mentioned above. In our sample installation we are going to create our own CA and we are going to sign that certificate signing request to produce a X.509 digital certificate.
The only problem with the previous scheme was that the client cannot be sure that the sender is who he claims to be and this is where a CA comes in as it is responsible for verifying the details of the sender and issuing the X.509 digital certificate to it. The X.509 digital certificate contains the sender's public key,domain identifiers,serial number for the certificate and most importantly the encrypted hashed(md5 hash, RSA encryption) data (Encryption is done using CA's private key,The hashed data encrypted using CA'S key serves as Digital signature of the CA). This constitutes sender's certificate.
The sender (server), when sending information to the client may choose to encrypt the entire contents or just calculate an SHA-1 hash and encrypt it using it's private key and sends the X.509 digital certificate it obtained from the CA along with this.
On the client side firstly the the CA is identified by 'CA attribute' in the X509v3 extension section of x.509 digital certificate, then using CA's public key (stored in the browser in the CA certificate public key info) the hash is decrypted and this decrypted hash is compared with the hash that is calculated over the rest of the x.509 digital certificate that was sent by the sender. If these hash values match then client can be sure that this certificate really was signed by the CA and hence can be sure of the server that is sending the data because it was signed by the CA. The client then can decrypt the contents of the message by using the public key found in the x.509 digital certificate.
There are many well known certificate authorities such as Verisign etc whose certificates are not to be signed by any authority as they are the root certificate authorities and there certificates already come pre-installed in the browsers like Firefox, Internet Explorer etc. you can view them in mozilla firefox by going to Tools->Options->Advanced-> Encyption and then choosing View Certificates.
The only concern with getting the certificate signed by a CA is the cost factor.But on the other hand, This trusted third party scheme is more secure because in case the sender(server) loses its private key then it can ask the CA to revoke its certificate doing so places the certificate in CRL (Certificate Revocation List) which ensures that no one else can pretend to be the sender.
It may happen that once in a while you may encounter that if you are viewing a site in mozilla you may encounter that mozilla displays you a warning message as shown below which warns you that you may be at risk viewing the website, this happens only due to the fact that the certificate may be self-signed by the server or a CA not known to the browser and therefore the authenticity of the sender cannot be known and hence you should avoid sending personal details over to a web server like that because if the private key of the server is compromised then it can lead to potential fraudulent activity. However, if you do trust the server you can click on proceed and this leads to saving of the CA certificate of the server's CA on your browser and then you can view the certificate as mentioned above. In our sample installation we are going to create our own CA and we are going to sign that certificate signing request to produce a X.509 digital certificate.

I hope this was informational enough theory and now we can really proceed with the installation of mod_ssl on apache.
4. Encryption Of Data (Shared secret key Encryption):-
The actual data b/w the client and the server is encrypted using shared secret key because it is faster and the server does not need to know the client's public key for encrypting the data that it sends to the client.
The key exchange however occurs through public key encryption as follows:-
As the client knows of server's public key so it generates a random secret key (to be used for encrypting the data) and then encrypts it using server's public key and on the server's end it uses its private key to decrypt the shared secret key. Hence the public key encryption scheme helps to transfer the shared secret key.
The actual data b/w the client and the server is encrypted using shared secret key because it is faster and the server does not need to know the client's public key for encrypting the data that it sends to the client.
The key exchange however occurs through public key encryption as follows:-
As the client knows of server's public key so it generates a random secret key (to be used for encrypting the data) and then encrypts it using server's public key and on the server's end it uses its private key to decrypt the shared secret key. Hence the public key encryption scheme helps to transfer the shared secret key.
5.Creating the x.509 digital certificate:-
To create the digital certificate we have to do the 5 following steps:-
To create the digital certificate we have to do the 5 following steps:-
- Generate the Server's Private and Public key
- Generate the CA's Private and Public key
- Generate the CA's x.509 Digital Certificate (Self-Signed)
- Generate the Server's Certificate Signing Request
- CA signing the certificate signing request
- Generate the Server's Private and Public key:- To generate the server's private key execute the following command in the directory above the directory that contains the OpenSSL module which in windows would be (if you have installed it using the windows binary) "C:\OpenSSL\bin" :-
- Generate the CA's Private and Public key:-
Repeat the same step as above and generate the private key for the CA and also encrypt this key. You will be asked for the pass-phrase for the key that would be required in case you want to use that key. Now execute the following command.
openssl genrsa -des3 -out CA.key 1024
- Generate the CA's x.509 Digital Certificate (Self-Signed):-
Execute the following command to generate a self signed x.509 digital certificate.
openssl req -new -x509 -key CA.key -out cacert.pem -days 1095
When you execute this command you would be asked for the pass-phrase of the key which you entered in the previous step so enter it and fill in the details asked for.
This command produces a self signed certificate(cacert.pem) using the encrypted rsa key CA.key with validity of 1095 days.
- Generate the Server's Certificate Signing Request:-
Now execute the following command to generate the server's certificate signing request (CSR).
openssl req -new -key server.key -out server.csr
Enter the details as requested and this will produce the csr that is sent to real CA authorities but in our case we are our own CA so we'll sign the certificate on our own.
- CA signing the certificate signing request:-
This command when executed will sign the certificate request server.csr to produce a x.509 digital certificate signed by our own CA.
openssl x509 -CA cacert.pem -CAkey CA.key -in server.csr -req -days 365 -out server.crt -CAcreateserial
This command signs the certificate signing request and note that the last option(CAcreateserial)is required because there has to be a serial file server.crl for CA to sign the certificate and is required only the first time.
openssl genrsa -out server.key 1024This command produces an private rsa key of 1024 bits long and you do not have to create a separate public key. You can choose to encrypt these key by adding -des3 oprion after the genrsa option which will encrypt this key by using 3-DES symmetric encryption standard.
6.Installing the certificate's and keys in proper directory:-
The certificate's and the key files should be installed anywhere outside the web root directory of apache like a directory c:/secret and placed in that directory. The certificate's should be installed outside of the directory because they are inaccessible to visitor of your site.
The certificate's and the key files should be installed anywhere outside the web root directory of apache like a directory c:/secret and placed in that directory. The certificate's should be installed outside of the directory because they are inaccessible to visitor of your site.
7.Setting up the Apache configuration(httpd.conf):-
There are many mod_ssl directives that you can implement i am just going to discuss some basic ones for more information there is an excellent tutorial available at this link www.modssl.org
Here's the sample configuration
Few of the mod_ssl directives:-
There are many mod_ssl directives that you can implement i am just going to discuss some basic ones for more information there is an excellent tutorial available at this link www.modssl.org
Here's the sample configuration
Few of the mod_ssl directives:-
- SSLEngine on/off :- This is the basic directive which enables or disables the ssl on apache. Prior to version 2 of apache this was called as SSLEnable /SSLDisable.
- SSLCertificateFile server_cert_file :- This specifies the certificate file for the server ie the server's x.509 digital certificate. Use /for absolute path or dir-name/file for the relative directory under the apache directory. In this case server.cert .
- SSLCertificateKeyFile server_key_file :-This specifies the private key file for the certificate file. In this case server.key .
- SSLCACertificateFile ca_cert_file:- This specifies the certificate file of the CA ie the CA's self signed x.509 digital certificate. Use /for absolute path or dir-name/file for the relative directory under the apache directory. In this case cacert.pem .
- SSLRequireSSL:- This forbids access to resource unless http over ssl is enabled for the current active connection.
- SSLProtocol (SSLv2,SSLv3,TLSv1,All):- By default all the protocols are enabled.You can disable a particular protocol like this: SSLProtocol all -TLSv1 which disables the Transport layer security protocol v1.
- SSLSessionCacheTimeout time_in_sec:- This sets the time in seconds till which the session key will be cached locally after which the key will be changed.
You can create a named host or a host based on ip address. In this we are going to setup the ip based virtual host.
Then we have to add the AddType directives so that apache recognizes the certificate files and their extensions. We will be adding the following two directives:
AddType application/x-x509-ca-cert .crt
AddType application/x-pkcs7-crl .crl
From the code box below just copy and paste the code into the httpd.conf.
But before that you would have to enable the mod_ssl module in the httpd.conf. To do that just open the httpd.conf and scroll down to the LoadModule directives and find one with the name mod_ssl and remove the # comment from before it as shown in the following figure.

From the code box below just copy and paste the code into the httpd.conf
############################################## ############# mod_ssl configuration ############ AddType application/x-x509-ca-cert .crt AddType application/x-pkcs7-crl .crl SSLEngine off #change this to directory where your certificate's are installed SSLCertificateFile conf/server.cert SSLCertificateKeyFile conf/server.key SSLCACertificateFile conf/cacert.pem #set the server to listen on port 8080 Listen 127.0.0.1:8080 <VirtualHost 127.0.0.1:8080> #enable ssl engine for port 8080 SSLEngine on SSLSessionCacheTimeout 300 SSLProtocol SSLv3 # here you can setup access to directories and authentication # by using the <directory dir_name=""> directive and AuthType,AuthName,etc ############################################## ############# end mod_ssl conf ############### </VirtualHost>
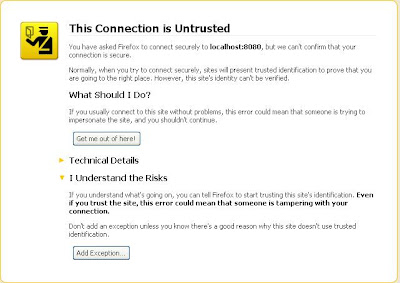
8. Testing the configuration:Now all you have to do is just open the browser and type in the url https://localhost:8080 and after which you will be displayed with a warning message by your browser as was mentioned before. The warning message look like the following in Mozilla Firefox.


You should add an exception for this after which the browser will download the CA certificate and you should see default apache web server page if successful. In mozilla certificate details can be seen by clicking on the navigation bar as shown below.

This is about it now we have set up and tested the SSL over http and hope this tutorial was helpful in making you understand the core concept behind digital certificates(X.509) public key encryption standard and setting up mod_ssl on your apache installation.